In this awesome presentation, Amit Malik discussed about the importance of return address in solving some of the problems related to analysis and detection of the malicious codes. Presentation:
You are browsing archives for
Category: Reverse Engineering
Reverse Engineering or Reversing
SecurityXploded 3rd Quarterly Meetup – 2
Here is the quick update and presentations from our recently concluded Third ‘SecurityXploded Cyber Security Quarterly Meetup’. In this meet, Sameer Patil delivered presentations on “Anatomy of Exploit Kits”, Satyam Saxena covered the topic on “Detecting the Malicious Url using Machine Learning” and Monnappa KA presented the topic on “Hunting the Gh0st RAT […]
SX 3rd Meetup – Hunting Ghost RAT Using
In this awesome presentation, Monnappa KA explained the details of Ghost RAT malware used in various Cyber Espionage attacks. He showcased the sandbox analysis, traffic pattern and decrypting the communications of Ghost RAT from packet capture. He also demonstrated both manual and automated method of detecting and decrypting the communications of Ghost RAT using memory […]
Announcing SecurityXploded 3rd Meetup –
This is an announcement for the upcoming SecurityXploded community meetup on 24th January 2015 in Bangalore, India. This meet is completely free and doesn’t require any registration or any other formalities to attend. The meet will start at 10 AM IST. After the meet, we will upload the presentations/videos for our online users to […]
Shellshock- the Destroyer
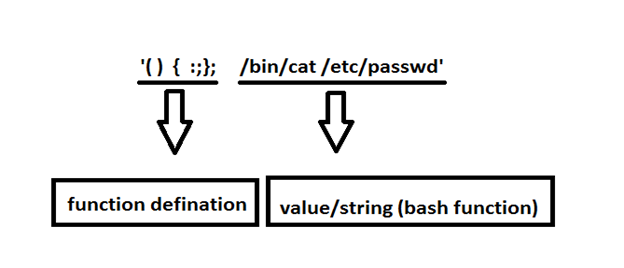
Shellshock – the latest vulnerability that was disclosed on 24 September 2014. Shellshock is also known as BASH Bug or Bashdoor. Firstly the original bug discovered by Stéphane Chazelas on 12 September 2014 and suggested the name “bashdoor” to it. Common Vulnerabilities and Exposures (CVE) identifier assigned to it is CVE-2014-6271. This bug exploit worldwide […]
Get Shell Access by bypassing ASLR and D...
Today’s Operating System uses various memory protection like DEP and ASLR. Microsoft enabled ALSR from 2007 to all its products. While Google and Firefox implement ASLR in 2010. We know that SEH exploitation is not possible in windows 7 and 8 due to DEP and ASLR. Yeah it is true but we can bypass ALSR […]
Detailed Overview of SEH
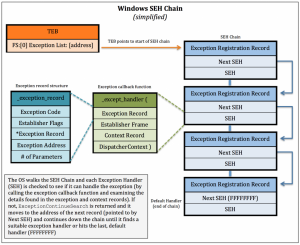
SEH stands for Structured Exception Handling developed by Borland and that gave license to Microsoft. This is the reason why SEH is available in Windows only. Exception is an error that disrupts the program execution. SEH is a software method of dispatching and handling exception, for software as well as hardware. If any exception occur […]
SecurityXploded 2nd Quarterly Meet – 27t
Here is the quick update and presentations from our recently concluded Second ‘SecurityXploded Quarterly Meet’. In this meet, Raghav Pande and Monnappa delivered fabulous presentations on reverse engineering the evasive tactics of advanced malwares and SecurityXploded Team announced the launch of a new project – MalwareNet – crowd based Malware Intelligence and Analysis […]
SX 2nd Meetup – Reversing and Decrypting
In this awesome presentation, Monnappa explained about Etumbot malware used in a Cyber Espionage attack. He showcased the sandbox analysis, Reverse engineering and Decrypting the communications of Etumbot Backdoor using practical video demonstrations. Presentation: Video Demo 1: Video Demo 2: Video Demo 3: References: http://www.arbornetworks.com/asert/2014/06/illuminating-the-etumbot-apt-backdoor/ http://www.fireeye.com/blog/technical/botnet-activities-research/2014/09/darwins-favorite-apt-group-2.html
SX Meetup 2 – Dissecting BetaBot
In this presentation, Raghav Pande explained various self defending mechanisms of BetaBot. He also presented unpacking, hooking and injection methods of this malware using illustrative screenshots. Presentation: